Creating a security framework that works
Even after a large number of data breaches over the last few years, I continue to hear questions about the relevance of cybersecurity best practices to small and medium-sized businesses.
Small business owners don’t believe their small business would be a target for cyber criminals. Let me settle the debate. Are cyber criminals targeting your small business? The answer is … yes.
Now, the question to consider is what should you do. Typically, the denial of a small business being a target is due to the cost of implementing countermeasures. At two recent conferences, speakers at both shared about the NIST cybersecurity framework and how it could be utilized by a smaller-sized business.
The cybersecurity framework was developed by NIST in conjunction with private industry. The framework isn’t designed to be one-size-fits-all. It is designed for organizations large and small to utilize it. The framework will allow organizations to determine activities that are important to their own critical service delivery allowing each individualized organization to prioritize investments to maximize the impact of each dollar spent.
Particularly for a smaller organization, the framework can look extremely overwhelming. However, it is actually structured in a way to help you and doesn’t have to be overwhelming. While it is a technical document, the framework was written with a common language and tried to minimize the technical jargon.
The overarching framework consists of three primary parts: the framework core, the implementation tiers, and the framework profiles. The core allows cybersecurity outcomes to be described across an organization. Elements of the core allow an organization to align itself with industry standards. The tiers provide a mechanism for organizations to view and understand the characteristics of their approach to managing cybersecurity risk.
Additionally, NIST was specifically asked by Congress to help small and medium-sized businesses. NIST created a cybersecurity resources road map. The road map points to four tiers, where the higher tiers point businesses that are more advanced in cybersecurity development to resources for their business, while the lower tiers point businesses with less sophisticated capabilities to resources as well. In order to determine which tier your business is in, it provides a couple of questions.
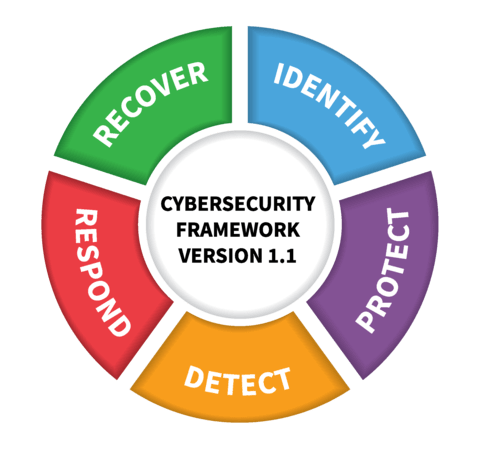
The framework identifies five overarching functions. The functions have categories with the categories having subcategories. Each of the function area is listed area with its NIST description and some additional information.
Identify – Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data and capabilities. Your first step is to identify what assets your organization has to protect.
Protect – Develop and implement appropriate safeguards to ensure delivery of critical services. Your second step is to consider what tools are available for you to protect those identified assets.
Detect – Develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The third step that an organization must consider is how it can detect if an incident occurs. Many organizations, especially small businesses, miss this step rendering much of the other areas moot.
Recover – Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The fifth and final component is to consider how you get back to normal operations if (or when) the incident occurred. If you don’t consider the recovery component ahead of time, your organization may not recover. Businesses have been forced to close for not planning on how to recover.
As mentioned, each function has several categories and subcategories to consider. While it may feel like a lot, your organization has a choice to either plan for what will very likely occur and recover the best way possible. Or leave it to chance. History says those organizations leaving it to chance may (or will) regret that decision.
If you would like to learn more about the NIST Framework, visit https://www.nist.gov/cyberframework. For additional NIST cybersecurity guides, you can visit https://csrc.nist.gov. NIST products are government funded and free for you to use. If all of these seems overwhelming, contact me. I can point you to local resources that can walk you through creating that cybersecurity plan for your organization.
Michael Ramage is the director of the Center for Telecommunications Systems Management (CTSM) at Murray State University. CTSM conducts research in the various areas of technology as well as serving as a liaison between the academic and private sectors. He can be reached at [email protected] or 270-809-3987 for questions or more information.
Originally published in the Four Rivers Business Journal and available at https://www.paducahsun.com/business/journal/creating-a-security-framework-that-works/article_ce512c4a-c599-50db-ac00-7f0ccc5a08ef.html